The booming cybercrime business
Cybercrime is poised to surpass illegal drugs as the primary source of income for criminal networks, according to experts. Here, we shed light on some of the methods used in digital crimes against Nordic consumers and businesses today.
What we’ve seen so far in 2024
| Phishing-as-a-service fraud tools served on a silver platter |
| Eavesdropping equipment used to scam private individuals |
| Generative AI opening new shortcuts for scammers |
| Fraudulent text messages are sent via the internet to bypass security filters |
| Safe-account fraud social manipulation to make you to think the criminals are from the police or bank |
| Scammers exploit updated LinkedIn information |
| Exploiting stolen usernames and passwords and targeting edge devices for cyber-attacks on Nordic businesses |
| Prevailing Nordic fraudulent SMS and calls 56.6 million fraud attempts via SMS and calls blocked in Norway alone in first half of 2024 |
Last year, when a Malaysian citizen was arrested in the Norwegian capital Oslo with a car filled with surveillance equipment, the Norwegian Police Security Service (PST) assumed it was a case of espionage.
However, it turned out to be part of a massive SMS fraud and a new method to bypass existing security filters.
Over the past year, cybercriminals have adopted an increasing number of non-traditional approaches to reach their victims, whether they are businesses or average individuals on the street.
Many of the individuals behind these phishing attempts and frauds are new as well. With significant help from AI, among other tools, new fraudsters connected to criminal networks are emerging across the Nordics.
Rise in fraudulent SMS and calls
The vast number of fraud attempts blocked by Telenor in the Nordics each day is clear proof of how big and serious a problem online crime is.
The people behind these fraud attempts are well-organised criminal networks that possess both the competence and resources to carry out sophisticated attacks on a large scale.
In Norway alone, Telenor blocked an astonishing 56.6 million attempts via text messages and calls in the first half of 2024.
In a survey conducted by YouGov on behalf of Telenor in March 2024, 1 in 2 Norwegian adults responded that they had experienced an attempt of digital crime in the first half of the year. In Finland, spam messages, fraud and phishing (SMS and email) are on top of the list of digital crimes experienced or seen as the biggest risk amongst consumers, according to DNA’s annual Digital Life 2024 survey.
This data illustrates the pervasiveness of cyber threats and underscores that fraud is a lucrative source of income for criminals, and many will go to great lengths to bypass the security measures set up by Telenor and other businesses. Criminals are constantly developing new methods and going to greater lengths to harm businesses and customers.
These findings are consistent with broader trends across the Nordic region, where digital security is a significant concern due to the region’s advanced technological infrastructure. With a highly developed digital economy, the Nordics are particularly vulnerable to such attacks, making robust security measures and continuous vigilance critical.
A positive development can be seen in Finland, where the authorities, telecom operators, and financial sector are collaborating closely to prevent the use of Finnish fixed and mobile telephone numbers in fraud and to reduce the number of foreign scam calls and SMS. The effort is based on three pillars: a technical solution validating if the call or SMS is legitimate or from a scammer, the implementation of regulation (1) from the Finnish Transport and Communications Agency, Traficom, on the interoperability of communications networks and services, and lastly, filtering by all Finnish telecommunications operators.
In addition to this, during spring 2024 Traficom has enabled the registration of protected SMS Sender IDs. This allows for example banks and financial institutions sending out SMS to Finnish citizens to register their SMS Sender ID in order to make sure that no one else can use the same one to falsify sender information.
While these national efforts are crucial, the broader European regulatory environment is also evolving to address these threats. The European Commission’s proposed third Payment Services Directive (PSD3) aims to harmonise the regulation of payment services across the EU. If adopted in its current form, PSD3 could strengthen fraud and consumer protection in our region. One of the key proposals includes fostering stronger co-operation between payment service providers and telecom operators to combat “spoofing” scams, where fraudsters impersonate employees in payment institutions. By encouraging this collaboration, PSD3 aims to ensure that both sectors work together more effectively to detect and prevent fraudulent activities, thus providing an additional layer of security for consumers. Further, PSD3 would also provide a robust legal framework for businesses to voluntarily share fraud-related data, further bolstering efforts to the monitor and prevent financial crime.

How businesses are being attacked
Our Security Operations Centres (TSOC) are critical components of efforts to protect business customers’ networks and equipment through monitoring, detecting, and responding to security threats. Recently, Telenor’s security centres have been handling an increasing number of serious incidents per month on average.
This includes both the prevention of ransomware attacks, and the removal of so-called “information thieves” in the network, which are being used by criminals to extract lists of usernames from the company’s network. As the value of crypto-currencies rise, we also note an increase in cryptojacking, where crypto-mining malware is attempted placed on a device to exploit the machine’s resources.
In addition to these attacks, we have also registered an increase in DDos attacks (distributed denial-of-service attacks) in the Nordics since the start of the Ukraine-Russia conflict. DDoS attacks aim to overload and paralyse servers and networks by flooding them with excessive traffic, thereby disrupting normal operations and potentially causing significant downtime for businesses. In the last year, our security centres have registered two particularly important trends in the ways businesses are attacked:
1) Stealing employees’ usernames and passwords
One of the most widespread methods used to attack businesses involves criminals taking control of and exploiting legitimate user accounts, rather than exploiting system weaknesses.
Examples of how this is done:
Attackers use leaked passwords from data breaches within other services, and match these with users who utilise similar passwords for their work accounts
Attackers try their luck with the most commonly used passwords across thousands of user accounts within different businesses
An employee is tricked into installing an “information thief” on their computer, which copies and sends out login details and session cookies to the attacker
An employee is tricked into submitting their username and password through a phishing scam
If the business utilises cloud services, such attacks can have serious consequences, as the attacker could gain access to many different systems through a single account.
To withstand these threats, businesses should implement measures such as two-factor authentication, hardware keys, certificate-based authentication, and passkeys with biometric sensors for PC and mobile devices.
2) Getting in through edge devices
Another method currently used by attackers is to actively target so-called edge devices within a business’ network.
These are endpoints in the network that are directly exposed to the internet, often because both employees and partners need easy access to documents and other information.
These include virtual private network (VPN) endpoints, mobile device management (MDM) servers, email servers and file-sharing servers. Many of these have limited security systems and can be compromised very easily.
After gaining access through such a unit, attackers can extract lists of usernames and gain deeper access to the network. To protect against this kind of attack, it’s important to have strong access controls and cloud monitoring. In addition, a good tip for businesses is not have more endpoints with open network access than are absolutely necessary.
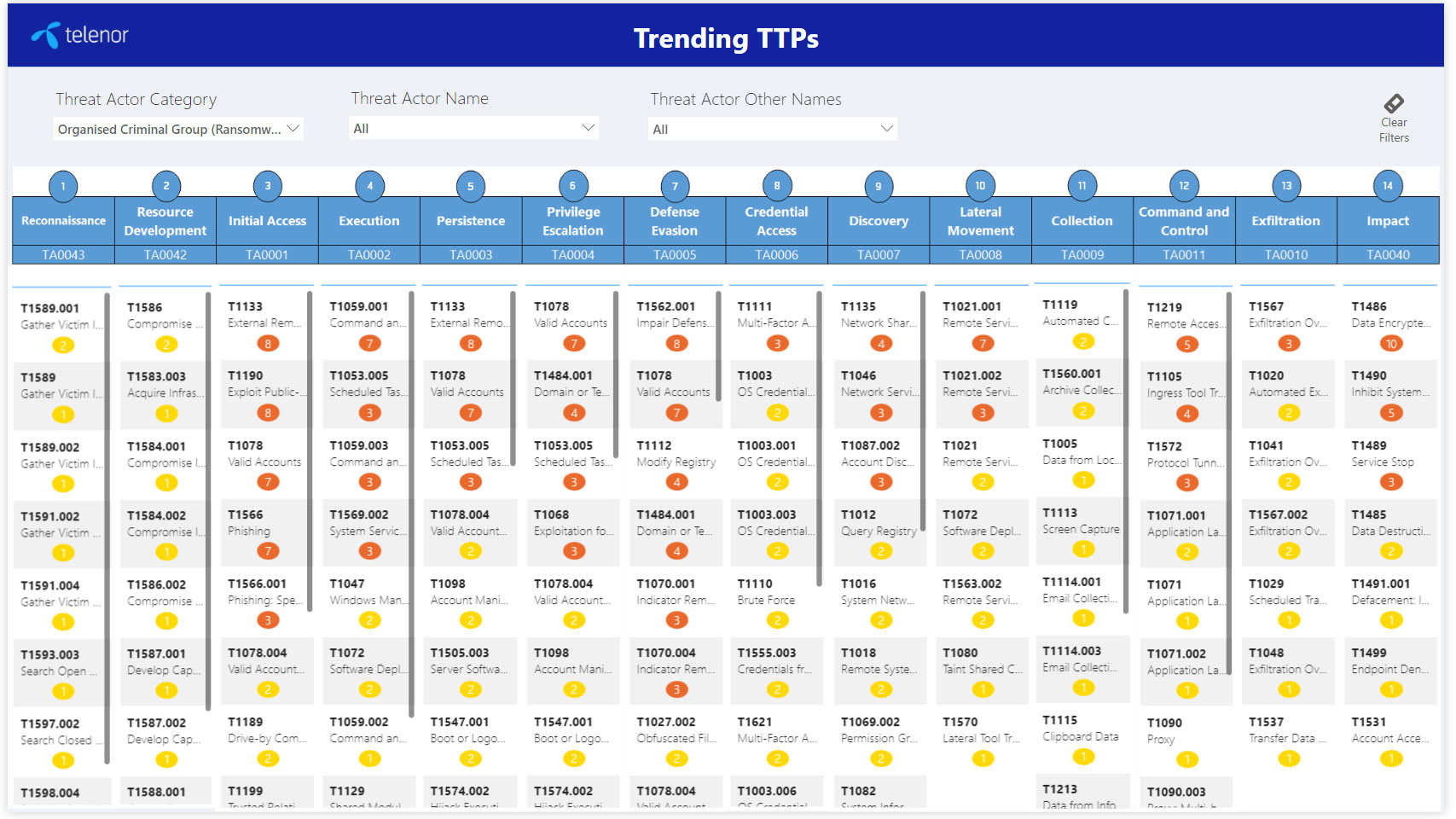
As shown in Figure 1, to protect against attack continued Threat Assessments are used to prioritise defences through kill chain analysis, using MITRE ATT&CK® to bind the threat landscape with frequency of identified methods of compromise.
Scammers exploit LinkedIn information
More recent fraud attempts indicate that criminals are paying close attention online to exploit newly available information to attack businesses and private individuals. Telenor has experienced that information from LinkedIn, in particular, is frequently used for this purpose.
The approach occurs almost in real time: Shortly after an employee has updated their profile with a new title, the employer’s HR department is contacted by criminals impersonating the employee. In the email, the HR department is asked to update the employee’s stored information with a new account number. When payday comes, the employee’s wages are mistakenly transferred to the account, which is controlled by the criminals.
A similar method, where fresh information is also used for scamming, has been used several times when people sell their used cars. In cases from Norway’s biggest online marketplace, Finn.no, the victims receive a false message from the Norwegian Public Roads Administration (Statens Vegvesen), instructing them to pay a fee as part of the sale or the transfer of registration.
Eavesdropping equipment used to scam private individuals
Among the tools and scam methods that were used in attacks against private individuals in the last year, we also find QR codes, artificial intelligence, new online services – and in the case of the aforementioned Malaysian citizen – an IMSI catcher.
The reason the Malaysian citizen drove around with eavesdropping equipment in the car was not to spy on the authorities or private citizens. He did it because it allowed him to send text messages to passersby without using the mobile network.
By using a so-called IMSI catcher, he created a direct connection to all of the nearby mobile phones. In this way, he was able to bypass Telenor’s security filters – as well as AI and SpamShield technology.
Many of the recipients of the messages were just random passersby who were busy with their holiday shopping. This increased the likelihood that people would be inattentive and thus respond quickly and uncritically to messages about undelivered packages or unpaid bills.
Currently, there is little indication that such equipment is actively being used by criminals on a large scale. Nevertheless, it illustrates how new methods are being used to bypass security mechanisms in mobile networks and in IT systems.
How the IMSI catcher was used
An IMSI catcher is a type of false base station used for surveillance of mobile communication by breaching the communication between mobile phones and the real base stations. IMSI stands for International Mobile Subscriber Identity, which is a unique identifier associated with every mobile phone that connects to a cellular network
It is generally illegal to use such equipment for anyone other than authorities that have been granted special permission
The device is often used for eavesdropping and espionage, but it can also be used to distribute text messages without using the mobile network. Essentially, the IMSI catcher tricks nearby mobile phones into connecting to it, enabling the interception and monitoring of communications and data from those devices
Last autumn, a Malaysian citizen was detained for having used an IMSI catcher in a vehicle to distribute fraudulent text messages to passersby in Bergen and Oslo, Norway
People in the vicinity of the IMSI catcher received a text message, seemingly coming from DHL, or the Norwegian banks DNB and Bank Norwegian. These messages led the recipients to a false website that requested their card information or prompted them to sign in with BankID, a personal electronic identification method in Norwayvolutpat, felis risus vehicula nunc, eu suscipit justo libero a libero. Praesent interdum dui non felis vulputate ultricies vitae id elit.
Use of QR codes in Denmark
QR codes have been increasingly utilised by scammers globally to carry out phishing attacks and other fraudulent activities. These scams often involve placing fake QR codes in public areas.
In recent developments, QR code scams have emerged as a threat in Denmark. The Danish police have in June 2024 issued warnings after incidents of fraud were reported at charging stations for electric vehicles. Scammers have been placing fake QR codes over the legitimate ones on these charging stations. When unsuspecting users scan these codes, they are redirected to fraudulent websites designed to steal their payment information or personal details.
These scams exploit the trust that people place in QR codes as a convenient way to access services quickly.
By mimicking legitimate websites, these fraudulent sites can easily deceive individuals into entering sensitive information, such as credit card numbers or login credentials. This trend highlights the growing need for vigilance when using QR codes, especially in public spaces where scammers may easily tamper with legitimate services. The Danish police advise the public to double-check the URLs they are directed to after scanning a QR code and to be cautious of any requests for payment or personal information that seem out of place.
Source: https://www.dr.dk/nyheder/indland/politietadvarer-mod-qr-svindelefter-snyd-paa-ladestandere
Text messages sent online: iMessage and RCS
Although Telenor blocks millions of digital fraud attempts every month, the increased awareness among Nordic people regarding suspicious links and security functions that block fake websites has made it more challenging for criminals to reach their victims this way.
This has led to many opting to use QR codes instead of links when they try to lure victims to fake websites.
However, a text message on the mobile phone is the most attractive and efficient bait to trick people into giving up their personal information – simply because many still fall for it.
As a result, the number of blocked fraudulent text messages has surged significantly. However, criminals are adapting to these defences. When Telenor blocks text messages with links to fake websites, criminals quickly try to find new ways to reach their goals.
This has led to a notable increase in fraud attempts via alternative messaging services. In other words, if you receive a suspicious message through iMessage (on iPhone), RCS (on Android) or WhatsApp, you should be extra cautious. Messages sent through iMessage or RCS (Rich Communication Services) on Android phones are sent with end-to-end encryption via the web.
The reason fraudsters target these channels is that Telenor and other operators are unable to block these messages, because they, like messages sent from an IMSI catcher, are not coming from the mobile network.
Phishing via undelivered packages still the most common The content you will find in phishing messages distributed on alternative channels can be about anything from exciting job offers to unpaid debt collection claims.
Messages about undelivered packages or a problem with an online order remain the most common ones. These messages are often used as the first part of both simple and more elaborate frauds.
A typical approach is to trick the recipient into thinking there has been an error regarding an order or a delivery, and then lure them onto a fake website or to a conversation with someone posing as a member of customer service.
This is where the victim will likely be tricked into giving up sensitive information such as credit card information or ID credentials. In some cases, scammers also use this opportunity to gain remote control of the victim’s computer and access further personal data.
Even if phishing through messages about undelivered packages is not a new thing, it remains an effective tactic for the scammers. This is why they are constantly refining the approach.
Tax refund scams are also widespread, with phishing emails and SMS messages mimicking the Finnish Tax Administration to steal banking credentials. The fraudulent messages often include links to realistic-looking phishing sites that collect personal information. These types of fraud are linked to organised crime networks that are increasingly combining digital tactics with traditional criminal activities. Finnish authorities, including NCSC-FI, continue to warn the public and provide guidance on staying safe.
This is how a phishing kit is used:
A legitimate website is cloned – for example www.telenor.se
The login and/or payment page is replaced with a script that steals login details and/or account information
The modified files are compressed to a .zip file and saved as a phishing kit
The phishing kit is uploaded to a hacked website or a fake domain – for example www.telenor-tjenester.top
Emails are distributed with links to this spoofed website
ChatGPT and chatbots specifically developed for criminal activity, such as WormGPT and FraudGPT, allow cyber criminals to quickly obtain information ahead of an attack.
Phishing-as-a-Service: Fraud tools served on a silver platter
Recently, several online services have appeared which have made the phishing method described above more efficient and streamlined. This has made it very easy for criminals to tailor so-called “fraud packs”—even if they have limited technical expertise.
The new scam platform Darcula is a prime example of this. The platform is a so-called phishing-as-a-service (PhaaS): a user-friendly online service that allows criminals to create and distribute messages based on pre-made templates with socalled phishing kits.
Unlike traditional phishing methods, Darcula uses modern technology such as JavaScript, React, Docker and Harbor—which makes it possible to always update and add new functionality without users having to reinstall the software.
The phishing kits offer users over 200 templates that disguise themselves as brands and businesses from more than 100 countries. These templates are generally high quality and come with local languages, logos and content to increase their credibility.
Darcula and platforms like it also make use of the aforementioned online detour, which sends the messages into the victims’ inbox via iMessage or RCS.
Generative AI: Opening new shortcuts for scammers Unsurprisingly, artificial intelligence is playing an increasingly important role in the everyday lives of both IT security specialists and criminals.
Among other things, ChatGPT and chatbots specifically developed for criminal activity, such as WormGPT and FraudGPT, allow cybercriminals to quickly obtain information ahead of an attack. This happens for example by asking the chatbot for all available information about a given company, including lists of suppliers and clients. This makes it possible to streamline the data collection process and the profiling of potential victims.
This technology has also made it easier to tailor and distribute fraud attempts across national borders, with far more realistic content in local languages than what was previously possible without large amounts of resources.
Meet the malicious GPTs
WormGPT is the Dark Web version of ChatGPT that enables the cybercriminal to quickly generate convincing phishing emails, malware, and malicious recommendations for hackers.
FraudGPT is a subscription-based malicious generative AI that uses sophisticated machine learning algorithms to generate deceptive content.
Traces to the criminal networks
Artificial intelligence, PhaaS services, and constant fine-tuning have made criminal approaches both more efficient and more easily accessible to far more people than before. An increasing amount of digital crime is found to be connected to Norwegian and foreign environments that have previously been associated with drug crime.
According to Sweden’s Economic Crime Authority (Ekobrottsmyndigheten), Swedish criminals now make more from fraud than drug sales. Last year alone, Swedish criminals made 5.6 billion SEK (0.5 billion EUR) through fraudulent activity.
There is little indication that things are different in neighbouring countries. Many of these frauds likely take place across borders. Among other things, the documentary series “Uppdrag granskning” by Swedish national public broadcaster SVT recently revealed a Swedish criminal network that committed extensive frauds on the elderly in both Sweden and across the border in Norway.
Phishing messages about online purchases were also used here, with subsequent frauds where bank accounts were drained – often by the scammers posing as someone working at the bank, claiming that they had to move the victim’s money to a “secure account”.
“Safe account fraud”
In Norway, the police issued a press release warning people against a similar approach where the criminals call victims, posing as police officers. In some cases, the criminals also showed up physically outside a victim’s residence to obtain their BankID (personal electronic identification method), bank cards and phones.
This winter, Telenor experienced a large increase in “social engineering” scam calls in which criminals posed as police officers. In just a single week in November, Telenor’s security filters picked up over 1.1 million unwanted calls in Norway. During any ordinary week the number would be at around 400,000. The increase is largely due to many cases of these police frauds over the phone. This type of scam is part of a broader trend of social engineering attacks across the Nordic region, where criminals exploit trust in authority figures and official institutions to commit fraud.
In Denmark, the total value of credit transfer fraud was DKK 333 million last year. Of this, approximately 81 per cent were scams of private or corporate account holders transferring money themselves (2). Even with the introduction and use of security measures such as two-factor authentication, fraudsters are continuously adapting their methods.
In the neighbouring country of Sweden, fraud is the category of crime that increased the most last year. According to the Swedish National Council for Crime Prevention, card fraud and fraud via social engineering, thereunder credit transfer fraud, increased the most among the fraud offences.
According to the police, this is how the scam unfolds over the phone:
The victim is first called by someone claiming to be from the police or Norwegian Authority for Investigation and Prosecution of Economic and Environmental Crime (Økokrim). They often tell the victim that they are about to be scammed, for example because someone has taken up a loan using the victim’s name
The phone call is then transferred to another criminal, who poses as someone from the bank who is there to help the victim
The victim is then prompted to offer their BankID authentication information and password and told to move their money to an allegedly safe account
The scammers then use the BankID information to access the victim’s online bank
If the transfer is stopped, for example by the bank, the scammer could approach the victim at their home and ask for the BankID device, bank card, phone or similar items
1 Update of Traficom’s Regulation 28 on the interoperability of communications networks and services.
2 Source: Finance Denmark, Nationalbanken
